A Guide to Staff Cyber Security Training for NZ Businesses
- Wade Kirkland

- Jan 13
- 10 min read
Good cyber security training does more than just tick a compliance box; it reframes your team from a potential liability into your most powerful line of defence. It’s all about teaching people how to spot, sidestep, and report common threats like phishing scams and credential theft.
For Kiwi businesses, getting this right turns security from a necessary chore into a real strategic advantage.
Why Your Team Is Your Strongest Cyber Defence
Let’s be honest. In most small or mid-sized organisations, the biggest cyber risk isn't some complex server hack. It’s a well-meaning staff member making a simple mistake.
Every single email they open, every link they click—these are the moments that truly define your company's security. Attackers know this, which is why they focus on exploiting human nature rather than just technical loopholes.
This is precisely why staff cyber security training is so critical. It’s not about just drumming a list of "don'ts" into people's heads. It’s about empowering them with the know-how and the confidence to make smart, secure decisions in the heat of the moment. A team that's clued-up becomes a human firewall, actively spotting and flagging threats before they can do any damage.
Turning People from a Risk to a Defence Layer
The real goal here is to build a proactive security culture. You want to get to a point where an employee’s first instinct on seeing a dodgy-looking email is caution, not a curious click. To get a better handle on the fundamentals, it's worth exploring a solid breakdown of What is Security Awareness Training?
When you achieve this shift in mindset, the payoff is huge:
Fewer Incidents: A team that can spot a scam is far less likely to fall for one. This directly cuts down the number of security headaches you have to deal with.
Faster Threat Spotting: Your people become an early-warning system, flagging suspicious activity that automated tools might have missed.
A More Resilient Business: When everyone plays a part in security, your whole operation becomes tougher and better able to bounce back from an attempted attack.
This flow shows just how critical that decision-making moment is for every employee, every day.
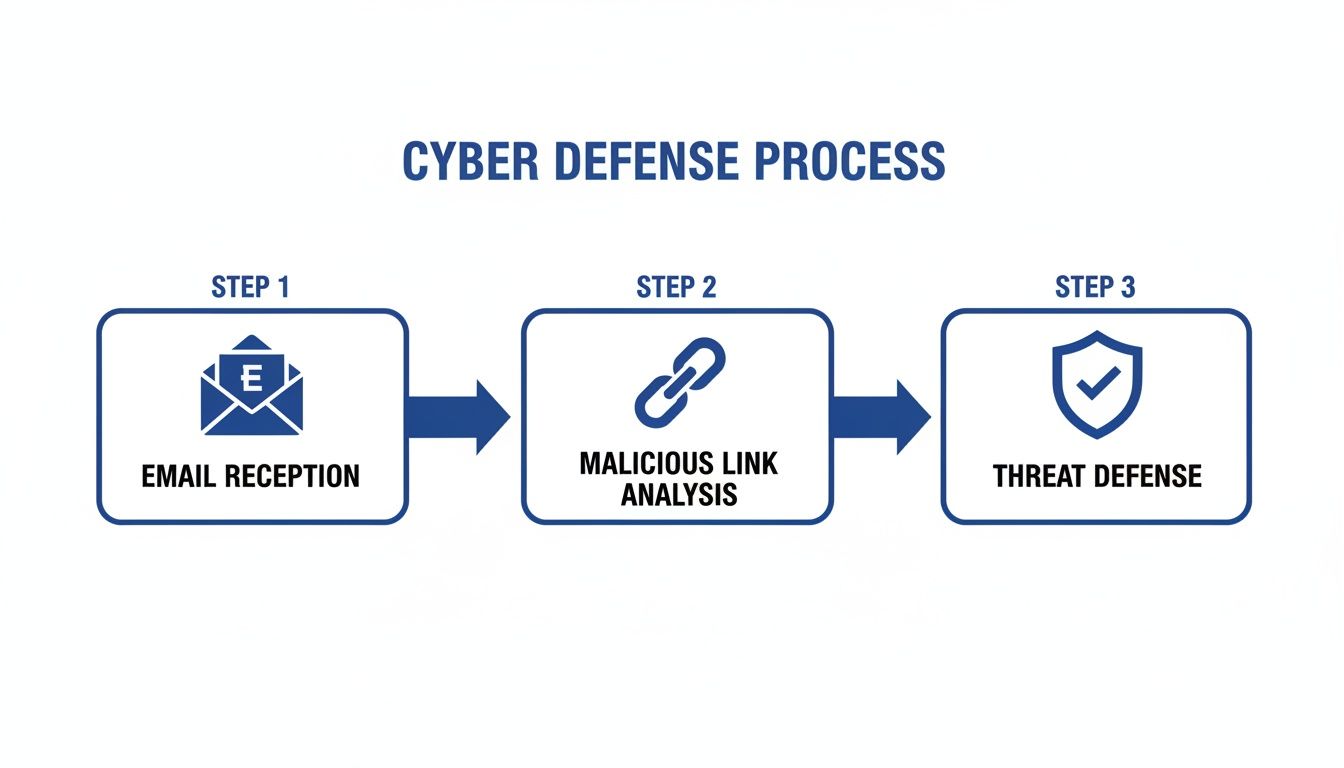
As the diagram shows, your entire defence can hinge on that split-second decision an employee makes.
If you want to dig deeper into protecting your business right here in Aotearoa, our essential SMB defence guide has some crucial insights on cyber security in New Zealand.
Pinpointing Your Team's Unique Security Risks

Generic, one-size-fits-all training just doesn’t cut it. Before you can build a programme that actually works, you have to get to the bottom of where your specific vulnerabilities are. This means digging for real data about your team's current knowledge and behaviours, not just making assumptions.
A great place to start is by looking at past security incidents and near-misses. Has someone in accounts nearly paid a dodgy invoice? Are people constantly reporting phishing emails? These events are goldmines of information, pointing you directly to your weakest links.
Anonymous surveys can also be incredibly revealing. Asking staff what they find confusing or difficult about security can uncover knowledge gaps you never knew existed. Remember, this isn't about blaming anyone; it's about finding opportunities to deliver better, more targeted education.
Identifying High-Risk Roles And Data
The reality is, not everyone in your business faces the same level of cyber risk. The next step is to figure out which roles handle your most sensitive information and what specific threats they run into every day. The goal here is to customise your training so it's directly relevant to their real-world jobs.
Take a look at this quick breakdown to see how a role-based approach can help you tailor training content for maximum impact.
Sample Role-Based Cyber Risk Profiles
Role | Primary Data Handled | Common Cyber Threats | Recommended Training Focus |
|---|---|---|---|
Finance Team | Invoices, bank details, payroll info | Business Email Compromise (BEC), invoice fraud | Recognising fake invoices, verifying payment requests |
Sales & Marketing | Customer lists, CRM data, prospect info | Credential theft, malicious links, phishing via social media | Spotting phishing in CRM, secure use of third-party apps |
Human Resources | Employee personal data, contracts | Data breaches, identity theft, insider threats | Data handling policies, privacy best practices, social engineering |
IT & Support | System credentials, network access | Ransomware, system exploits, advanced threats | Privileged access management, incident response drills |
Mapping out these risks helps you move away from treating security as one giant, overwhelming topic. Instead, you can deliver focused, relevant training that solves the actual problems your people face daily.
This role-based approach makes the training immediately useful and helps your team see how the lessons apply directly to their tasks. When you combine this human-focused understanding with technical assessments, you create a much stronger defence.
To get a clearer picture of your technical weak spots, it's worth exploring how penetration testing can uncover the hidden vulnerabilities in your systems.
Building Your Core Cyber Security Curriculum
Now that you’ve mapped out your organisation’s unique risks, it’s time to actually build the foundation of your cyber security training. A good curriculum isn’t just a list of rules; it’s about giving your team the context and real-world examples they need to connect security with their day-to-day jobs. The goal here is to make security an instinct, not just another box to tick.
A brilliant place to start is with the human element. So many attacks are designed to play on our natural instincts like trust and urgency, so your training needs to hit those psychological triggers head-on. Use scenarios your team will genuinely recognise, like a dodgy-looking invoice from a supplier or one of those scam texts pretending to be from NZ Post about a missed delivery.
The numbers coming out of New Zealand show just how critical this is. CERT NZ dealt with 1,968 incidents in the first quarter of 2023 alone—that's a 12% jump from the quarter before. Digging deeper, there was a worrying 35% surge in unauthorised access cases, many of which started with simple human error. Targeted training is what stops these mistakes from happening. You can get more detail on these trends and discover insights from the CERT NZ report.
Must-Have Training Modules
Your curriculum should be built around the most common threats Kiwi businesses are facing right now. Think of these modules as the non-negotiable building blocks for your programme.
Phishing and Social Engineering: This is ground zero. Teach staff to spot the classic red flags—weird sender addresses, overly urgent language, unexpected attachments. But don't just stop at emails. Make sure you cover SMS phishing (smishing) and voice phishing (vishing) too.
Strong Password and Credential Management: This is all about digital hygiene. Cover the basics of creating complex, unique passwords for different systems. Crucially, show them how to do this without going crazy by introducing them to a good password manager. And, of course, hammering home the importance of multi-factor authentication (MFA) is a must.
Secure Remote Work Practices: With so many people working flexibly, this isn't optional anymore. Your training has to cover securing home Wi-Fi, the dangers of using public networks for work, and clear company policies around using personal devices.
The best training I’ve ever seen moves past theory and gets practical. Show your team a real (but sanitised) phishing email that your filters caught. Break down exactly why it’s malicious and walk them through what would have happened if someone had clicked that link. It makes the threat real.
To create a truly robust curriculum, you also need to cover the fundamentals that protect your core systems. For any teams that touch your cloud environment, for instance, that means building in training on key AWS security best practices.
Choosing Training Methods That Actually Engage Your Team
How you deliver your staff cyber security training is every bit as important as what you teach. We’ve all seen it: a dry, click-through slideshow that people race through just to tick a box. That approach guarantees your team will forget everything the moment they close the window.
The real goal is to make security an ongoing, engaging conversation, not a dreaded annual chore. To do that, we need to focus on active participation and real-world application. From what we've seen, a blended approach that mixes different formats almost always gets the best results by accommodating different learning styles and packed schedules.
Finding the Right Mix for Your Team
Instead of putting all your eggs in one basket, a combination of a few key methods keeps the learning fresh and makes it stick. A great strategy is to use a central platform to track everyone's progress and assign different activities. Many organisations find that effective monday.com training and support (https://www.wiselyglobal.tech/monday-training-and-support) gives them the structure they need to manage these multi-faceted learning programmes.
Here are some of the most effective methods we recommend building into your mix:
Interactive E-Learning Modules: These are often the foundation of a good programme. The key is to look for modules with quizzes, branching scenarios, and video content that keep people actively involved rather than just passively reading.
Live Workshops (Virtual or In-Person): Nothing beats a live session for tackling complex topics or allowing for real-time questions. We find workshops are fantastic for deep-diving into social engineering, where you can role-play scenarios and have genuine back-and-forth conversations.
Microlearning: This is all about delivering security know-how in small, digestible chunks. Think short videos (under three minutes), infographics, or quick email tips sent out weekly. It’s the perfect way to reinforce key concepts without overwhelming your team.
Phishing simulations are non-negotiable. Frankly, they are the single most effective way to provide safe, hands-on practice. When an employee clicks on a simulated malicious link, it creates a powerful, private learning moment that theory alone can never replicate.
Ultimately, the best delivery method is the one your team will actually engage with. You don't have to boil the ocean on day one. Start small, get feedback from your staff, and be ready to adjust your approach.
When you make training relevant, varied, and respectful of your team’s time, you start building a culture where security awareness becomes second nature.
Measuring the Impact of Your Security Training
So, you've invested time and money into staff cyber security training. How do you actually know if it's paying off?
Simply ticking a box to say someone has completed a module just doesn’t cut it. The real goal is to measure tangible, lasting changes in behaviour. We need to move beyond simple completion rates and focus on metrics that prove your team is genuinely becoming a stronger human firewall.
This is all about shifting your focus to Key Performance Indicators (KPIs) that directly reflect a more secure mindset. Instead of just seeing who finished the training, you can start tracking meaningful data that shows the programme is actually working.
Key Metrics for Behavioural Change
To truly gauge how effective your training is, you need to look for measurable actions that show people are thinking differently about security. A great programme will produce clear, positive trends in these areas.
Phishing Simulation Click-Through Rates: This is your most direct measure of success. A steady decrease in the percentage of employees clicking on your simulated phishing links over time is a clear win. It shows the message is sinking in.
Suspicious Email Reporting Rates: Paradoxically, you want this number to go up. An increase in staff actively reporting potential threats is a fantastic sign. It means they're shifting from being passive targets to proactive defenders for the business.
Quiz and Assessment Scores: Short, sharp quizzes after a training module can quickly confirm knowledge retention. This helps you pinpoint specific topics that might need a bit more reinforcement down the line.
For Kiwi businesses, this proactive defence is more critical than ever. In 2023, financial losses from cyber crime in New Zealand shot up 19% to $20 million in a single quarter, with phishing and credential harvesting leading the attack. You can dig into more of these NZ cyber crime statistics to see the scale of the problem.
Don't forget the power of qualitative feedback. Simple, anonymous surveys asking questions like, "What was the most useful thing you learned?" or "What security topic still feels confusing?" can provide invaluable insights to help you fine-tune your approach for the next round of training.
Common Questions About Staff Cyber Security Training

When you're rolling out a new security programme, it's completely normal for questions to bubble up. The first time through can feel a bit daunting, so we've pulled together some of the most common queries we hear from NZ business owners to give you clear, straight-up answers.
Our aim is to help you build your staff cyber security training with confidence, making sure you’re tackling the right issues from day one.
How Often Should We Conduct Security Training?
Effective security training is never a one-off event. The threat landscape simply changes too fast for a "set and forget" approach to work.
Best practice is to blend a comprehensive annual training session with ongoing, bite-sized reinforcement throughout the year. Think of it as creating a constant learning cycle.
Annual Deep Dive: A thorough session covering the core principles and any new threats that have emerged.
Ongoing Reinforcement: Things like monthly phishing simulations or short, weekly security tip videos are perfect for keeping awareness high.
Immediate Onboarding: New hires need foundational training as soon as they start, ideally before they get full access to your systems.
This rhythm keeps security front-of-mind and ensures your team’s knowledge stays current as new threats appear, both in New Zealand and around the world.
What Is the Biggest Mistake Businesses Make?
By far, the most common pitfall we see is treating training as a box-ticking compliance exercise. This almost always leads to using generic content that has zero relevance to an employee's actual day-to-day job.
When training is boring, overly technical, or lacks scenarios your team can actually relate to, people switch off. They might click through the module to get it done, but they won't retain the information or, more importantly, change their behaviour. To be effective, your training has to be tailored to your business and the real threats your people face.
The moment your team sees a training scenario they recognise from their own inbox, the lesson clicks. Generic examples about fictional overseas companies just don't have the same impact. Customisation is everything.
How Do We Get Leadership Buy-In?
Getting management on board is often about reframing the conversation. Don't position training as an IT cost; frame it as a crucial investment in risk management and business continuity.
Build your case with real data. Point to local statistics, like the millions of dollars in losses reported by CERT NZ from Kiwi businesses, to show the tangible financial risk of a single breach. Then, present a clear, concise plan that outlines:
The specific risks you want to address.
The training methods you'll use (e.g., simulations, workshops).
How you'll measure success—for instance, targeting a 20% reduction in phishing simulation clicks within six months.
Is Cyber Security Training Expensive for Small Businesses?
It definitely doesn't have to be. While there are comprehensive enterprise-level platforms out there, you can build a very effective foundation on a modest budget.
The key is to be strategic. Start with the excellent free resources provided by government bodies like CERT NZ. You can combine these with targeted, in-house workshops that focus on your biggest risks and add a subscription to a cost-effective phishing simulation tool.
The initial cost of basic training is tiny when you weigh it against the potential financial and reputational damage of just one successful breach.
At Wisely, we help New Zealand businesses build resilient and secure operations. Our experts can help you design, implement, and manage a staff cyber security training programme that delivers measurable results. Find out how we can strengthen your human firewall at https://www.wiselyglobal.tech.
Comments