A Complete Guide to Cyber Crime NZ for Business Protection
- Wade Kirkland

- 2 days ago
- 17 min read
Cybercrime in New Zealand is a serious, fast-growing problem. We’re not just talking about minor inconveniences, either—reported financial losses are hitting millions every single quarter.
At its core, cybercrime is any criminal act that targets or uses a computer, network, or connected device. For businesses, the impact can be devastating, leading to financial theft, major operational disruption, and severe reputational damage.
Understanding the Modern Cybercrime Landscape in NZ
Let’s be clear: cybercrime isn’t just an IT issue anymore. It’s a fundamental business risk that every organisation in New Zealand has to face head-on. The threats are constantly changing, from crafty phishing schemes designed to steal passwords to crippling ransomware attacks that can shut your entire operation down.
The costs, both financial and otherwise, can be huge. It's not just about the money you might lose; it's about the erosion of customer trust and the long-term damage to your brand. For any Kiwi business leader, getting to grips with this environment is the absolute first step toward building a solid defence. That means knowing the most common threats you’re up against and understanding your legal responsibilities.
Key Defence Principles
A strong cybersecurity strategy really comes down to a few core pillars. Think of these as the foundation for everything we'll cover in this guide:
Proactive Technical Measures: This is about getting the essentials right. Things like multi-factor authentication, solid firewalls, and keeping all your software up to date are non-negotiable for protecting your digital assets.
Compliant Reporting and Response: When something does go wrong, you need a plan. Knowing the right way to report an incident to authorities like CERT NZ and the Police, as required by the Privacy Act, is crucial.
Building a Security-First Culture: Your people are your best defence. Training your team to spot and report suspicious activity turns every employee into a guardian of your business.
CERT NZ is the go-to government agency for guidance and incident reporting. It’s a fantastic resource.
This official portal is the central hub for businesses and individuals to report cyber security issues, get alerts on new threats, and find practical advice. If you're looking to dive deeper into building out your security plan, check out our comprehensive guide to cyber security for companies in NZ.
Common Cyber Attacks Targeting NZ Businesses
To build an effective defence, you first need to know what you’re up against. While cyber crime in New Zealand comes in many shapes and sizes, a few key attack types consistently cause the most headaches and financial pain for local businesses. Getting your head around these methods is the first critical step in training your team and putting the right security measures in place.
The fallout from a successful attack goes well beyond the initial cash grab. It hits a business from multiple angles, as this infographic shows.
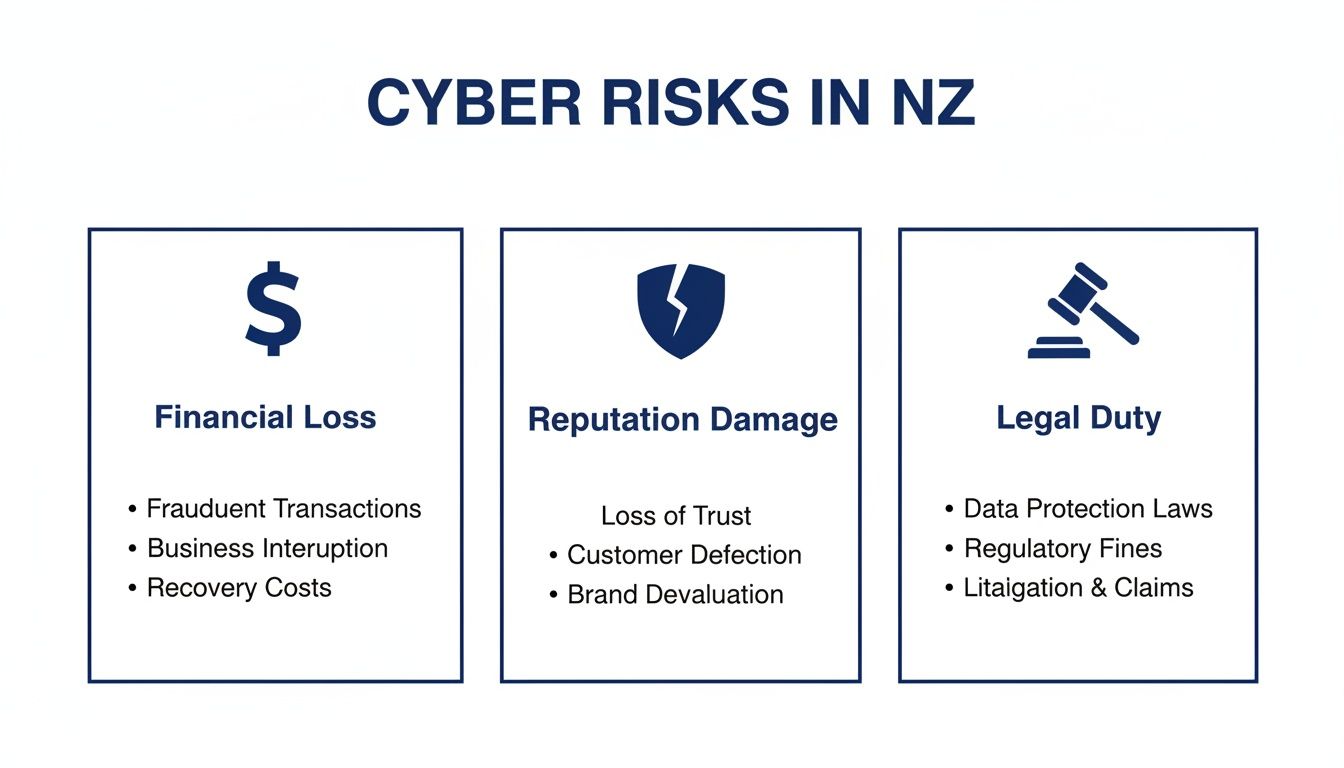
It’s a sobering reminder that on top of the direct financial hit, the damage to your brand’s reputation and the failure to meet your legal duties can have serious, long-lasting consequences.
To give you a clearer picture, here’s a quick rundown of the threats we see most often.
Common Cyber Threats Targeting NZ Businesses
This table summarises the cyber attacks that frequently target New Zealand businesses, outlining what the criminals are after and how it typically impacts day-to-day operations.
Threat Type | Primary Goal | Common Business Impact |
|---|---|---|
Phishing & Spear Phishing | Steal credentials, personal data, or financial information. | Unauthorised system access, data breaches, fraudulent transactions. |
Ransomware | Encrypt data and extort money for its release. | Complete operational shutdown, data loss, severe financial strain. |
Malware & Spyware | Disrupt operations, steal information, or gain system control. | Data theft, system degradation, unauthorised surveillance of activities. |
Business Email Compromise | Deceive staff into making unauthorised fund transfers. | Significant direct financial loss, supply chain disruption, trust erosion. |
Understanding these different angles of attack helps you see where your own business might be vulnerable.
Phishing and Spear Phishing
At its core, phishing is a con game. Attackers try to steal sensitive info—think login details or credit card numbers—by posing as a legitimate organisation in an email, text, or message. They often create a false sense of urgency or panic to bait people into clicking a bad link or opening a dodgy attachment without thinking.
Spear phishing is the targeted, more personal version of this. Instead of blasting out thousands of generic emails, the attacker does their homework on a specific person, department, or company. This research allows them to craft an incredibly convincing and personalised message that’s much harder to spot.
Business Impact: Stolen credentials, unauthorised access to company systems, data breaches, and direct financial fraud.
Practical Example: An accounts team member gets an email that looks like it's from their CEO, urgently asking for the company's latest creditor report. The tone and signature look right, but a closer look would reveal the sender's email address is just one letter off from the real one.
Ransomware Attacks
Ransomware is nasty stuff. It’s a type of malicious software that gets into your system and encrypts all your files, locking you out completely. The attacker then pops up with a ransom demand, usually in cryptocurrency, for the key to unlock your data. There's absolutely no guarantee you'll get your files back if you pay, and it often just marks you as a willing target for future attacks.
This type of cyber crime has become incredibly destructive for NZ businesses, capable of grinding all operations to a halt for days or even weeks. Getting back on your feet is almost always a complex, expensive, and stressful process that requires expert help.
Malware and Spyware
Malware is the catch-all term for any software written with malicious intent—to cause damage to a computer, server, or network. This family includes everything from old-school viruses and worms to sneaky trojans that disguise themselves as legitimate programs.
Spyware is a particularly stealthy type of malware. It installs itself on a computer and quietly records everything the user does, from keystrokes to website visits, and sends that information back to the attacker.
Business Impact: Data theft, slow or crashing systems, operational disruption, and covert surveillance of confidential business activities.
Practical Example: A staff member downloads a "free" design tool they found online. Buried in the installation is a spyware program that starts logging every key they press, eventually capturing the login details for the company’s online banking portal.
Business Email Compromise (BEC)
Business Email Compromise (BEC) is a highly sophisticated scam aimed squarely at businesses that make regular payments or wire transfers. Criminals gain access to a company email account and then impersonate the real owner to trick an employee, a supplier, or a partner into sending money to a bank account they control.
A classic BEC tactic is invoice fraud. The attackers intercept a real invoice from one of your suppliers, alter the bank account details to their own, and then send it on to your accounts payable team. Because these scams prey on human trust and established procedures, they can often slip right past technical security filters.
A Look at Recent Cyber Crime Trends and Statistics in NZ
If you want to effectively defend your business, you first need to understand what you're up against. Digging into the recent data on cyber crime in NZ gives us a clear picture of how criminals are operating, who they're targeting, and the real-world financial damage they're causing. This isn't just about looking at numbers on a page; it's about turning national statistics into practical intelligence you can use to protect your organisation.
The data is telling us a pretty clear story: cyber attacks are becoming more frequent, and they're hitting businesses harder in the pocket. For any business owner or manager, this means the risk of a major financial loss from a single security incident is higher than it's ever been. By getting a handle on these trends, you can start making smarter decisions about where to invest in security and how to protect your most critical operations.
The Financial Toll and Top Attack Vectors
The latest figures paint a pretty stark picture of the escalating financial cost. New Zealand businesses really felt the pain in the first quarter, with official data showing 1,369 incident reports were triaged. The direct financial losses from these attacks shot up to a staggering $7.8 million. That’s a sharp 14.7% jump from the $6.8 million reported in the previous quarter—a statistic that should be a serious wake-up call for finance and IT leaders across the country. For a more detailed breakdown, you can dive into the full Q1 report for cyber security insights from the NCSC.
So, what's driving these losses? It comes down to a few specific, well-practised attack methods.
Phishing and Credential Harvesting: These old favourites led the charge, jumping 15% from the last quarter to 440 incidents. This was by far the sharpest increase across all reported categories.
MFA Bypass: Attackers are getting smarter, using sophisticated tricks to get around Multi-Factor Authentication, which puts any business workflows that rely on email directly in the firing line.
Operational Disruption: Think about your sales teams tracking leads or your project managers coordinating tasks. When their communication channels are compromised, the entire operation can grind to a halt.
What this data really shines a light on is the human element. Attackers are having a lot of success simply by exploiting routine business processes and tricking staff into handing over their login details.
The consistent rise in phishing-related losses shows that even with technical safeguards, attackers are winning by manipulating employee trust and exploiting standard business communications.
What This Means for Your Business
These statistics aren't just abstract figures; they are a direct warning. The sheer volume of credential harvesting attacks means that any business using email for sensitive operations—from sending invoices to managing customer relationships—is a prime target for cyber crime nz.
It’s a clear signal that basic security measures just don't cut it anymore. Protecting your organisation demands a multi-layered defence that brings together solid technical tools with ongoing staff training. Your team needs to be able to spot and report suspicious activity, transforming your biggest potential weakness into your strongest line of defence. The trends are clear: without this combined approach, Kiwi businesses remain dangerously exposed to significant financial and operational damage.
The Escalating Threat of High-Impact Financial Scams
It’s easy to get fixated on malware and broad-stroke cyber attacks, but some of the most devastating threats Kiwi businesses face are actually far more personal. We’re talking about highly targeted financial scams. These aren't just random shots in the dark; they are carefully planned operations designed to exploit the one thing your software can’t patch: human trust.
Two of the most common and costly threats are Business Email Compromise (BEC) and sophisticated invoice fraud. These attacks don't rely on fancy hacking tools. Instead, they weaponise social engineering, making them incredibly difficult for standard security filters to catch. Criminals do their homework, identifying key people in your finance team and impersonating CEOs, partners, or trusted suppliers to get fraudulent payments authorised.

Because these scams often come from legitimate (albeit compromised) email accounts and perfectly mimic real business conversations, they sail right past typical security checks. The fallout can be financially crippling.
How These Scams Unfold in Practice
Let’s look at a classic, real-world example. Your accounts person gets an email from what looks like a long-term, trusted supplier. The email looks completely legit—logo, signature, the lot. It politely informs them that the supplier has changed banks and asks for all future payments to be sent to a new account number.
The request seems routine enough, so the employee makes the change. It's often not until weeks later, when the real supplier calls to chase overdue invoices, that the business realises it has been sending thousands—sometimes hundreds of thousands—of dollars straight into a criminal's pocket.
This scenario plays out all too often, exposing a critical weakness in the internal controls of many New Zealand organisations.
The recent explosion in high-value financial scams shows a clear shift in tactics. Criminals are no longer just after your data; they are aiming directly for your cashflow by exploiting the human trust at the heart of your financial processes.
The financial damage is getting worse at an incredible rate. The third quarter of last year was a particularly brutal one for New Zealand businesses. The NCSC recorded NZ$12.4 million in direct financial losses—a shocking 118% increase from the previous quarter. This spike was driven almost entirely by business email scams and dodgy transfers, where just a handful of major incidents made up 94% of the total losses. You can read more about how these attacks are hitting Kiwi businesses in the latest security findings on SecurityBrief.
Building a Stronger Defence
Protecting your business from these kinds of scams takes more than just good technology. It comes down to rock-solid internal processes and fostering a healthy culture of scepticism and verification.
Implement Multi-Person Approval: Make it a rule that no single person can change supplier payment details or authorise a large, unusual transaction. Always require a second set of eyes.
Verify Requests ‘Out-of-Band’: If you get an email asking to change bank details or make an urgent payment, always verify it through another channel. Pick up the phone and call a known, trusted contact number for that supplier—not the number in the email signature.
Conduct Regular Staff Training: Your team is your best defence. Make sure everyone, especially those in finance and admin roles, understands the tell-tale signs of BEC and invoice fraud.
By weaving these simple checks and balances into your day-to-day operations, you create crucial roadblocks that can stop a fraudulent payment dead in its tracks, before the money is gone for good.
Your Legal Obligations and Reporting Channels in NZ
When a cyber attack hits, the ensuing chaos can make it incredibly tough to think straight. That's why understanding your legal duties and the correct reporting channels before anything happens is absolutely critical for any New Zealand business. Getting it wrong doesn't just slow down your recovery; it can land you in hot water legally and financially, piling more damage on top of the original attack.
Dealing with the aftermath of cyber crime in NZ is about more than just the technical fix. It’s about communicating compliantly with the right people. The laws here are set up to protect people’s private information and to help keep an eye on national security threats.
The Privacy Act and Notifiable Breaches
The main piece of legislation you need to know is the Privacy Act 2020. It’s pretty straightforward: if your organisation holds personal information, you have to take reasonable steps to protect it from being harmed, lost, or accessed by the wrong people. This isn't just a friendly suggestion—it's the law.
If your business has a data breach that is likely to cause serious harm to someone, you are legally required to report it. This is what’s known as a notifiable privacy breach.
What counts as "Serious Harm"? Think financial loss, identity theft, threats to someone’s safety, or even significant emotional distress.
Your Reporting Duty: You must tell both the Office of the Privacy Commissioner and the people affected as soon as you practicably can.
Failing to report a notifiable breach can lead to fines of up to $10,000, and that’s before you even get to other potential damages.
"So many businesses underestimate their responsibilities under the Privacy Act. It’s not just about stopping breaches from happening, but about having a clear, compliant plan for when one inevitably does. Quick and honest reporting is simply non-negotiable."
Who to Report Cyber Crime To
Knowing who to call first can make all the difference in mounting an effective response. Different agencies look after different parts of a cyber incident, and getting in touch with the right one quickly can dramatically change the outcome for your business.
Here’s your primary contact list for reporting cyber crime in NZ:
CERT NZ (Computer Emergency Response Team): Make this your first call for any cyber security incident, whether you think a crime has been committed or not. They give expert advice, help you figure out what you're dealing with, and can guide your technical response. They also gather data to see the bigger picture of what's happening across the country.
NZ Police: If you've lost money or believe a specific crime has occurred (like theft, fraud, or ransomware extortion), you must report it to the Police. They’re the ones who investigate the criminal side of the attack.
Office of the Privacy Commissioner (OPC): As we covered, if personal information has been caught up in a breach that’s likely to cause serious harm, you have a legal duty to notify the OPC.
It's also worth remembering that these agencies all work together. Reporting to CERT NZ can often make your report to the Police a lot smoother, as they can help you pull together the technical details needed for an investigation. By following these channels, you’re ensuring your response is both compliant and well-structured from the get-go.
Developing a Proactive Cyber Defence Blueprint
Making the shift from simply being aware of cyber threats to actively preventing them is probably the single most important step any NZ business can take. A proactive cyber defence blueprint isn't about throwing money at the most expensive software on the market; it's about building smart, practical layers of defence that protect your entire operation, from the ground up. This framework should combine essential technical controls with a strong, security-focused company culture to create a truly resilient posture against common forms of cyber crime in NZ.

The scale of the problem here in New Zealand is growing. Over the past year, the National Cyber Security Centre (NCSC) had to handle nearly 6,000 incident reports. Ransomware was a huge driver behind these incidents, causing direct financial losses of $26.9 million. It was the small and medium-sized enterprises (SMEs) that were hit hardest, with more than half reporting at least one threat. Often, this was because they were missing basic protections like MFA or didn't have solid backups in place. You can get the full picture by exploring the national report to understand the growing cyber threats New Zealand faces.
This reality really highlights why you need a structured plan. A great place to begin is by using a comprehensive cybersecurity risk assessment template to understand where your specific vulnerabilities lie.
Foundational Technical Controls
Let’s start with the non-negotiables. These technical measures are the bedrock of any solid security strategy, and the good news is, they're surprisingly cost-effective to get in place.
Multi-Factor Authentication (MFA): This is a must. Enforce MFA across all your critical systems—especially email, financial software, and any remote access portals. It adds a crucial layer of security that can stop criminals in their tracks, even if they somehow manage to steal a password.
Consistent Software Updates: Keep everything patched. That means all your operating systems, applications, and network devices. Attackers absolutely love to exploit known vulnerabilities in outdated software, which makes timely updates one of your simplest and most effective defences.
Reliable Data Backups: Implement the 3-2-1 backup rule. That's three copies of your data, on two different types of media, with one of those copies stored safely off-site. Critically, you need to test your backups regularly to make sure you can actually restore your data when you need it most.
When these controls work together, they drastically shrink your attack surface, making it much, much harder for criminals to find a way into your systems.
Creating a Security-First Culture
Of course, technology alone will never be enough. Your people are your first and last line of defence, which makes ongoing training an absolutely critical part of your blueprint. A security-first culture is one where every single person on your team feels a sense of responsibility for protecting the business.
A well-informed team member who can spot a dodgy email is often more effective than the most expensive firewall. Human intuition, when it’s backed by solid training, is a powerful weapon against the social engineering tactics that are behind so many attacks.
To build this kind of environment, you need to provide regular, engaging training that goes beyond a dry, once-a-year presentation. Cover the common threats like phishing, invoice fraud, and secure password habits. It’s also vital to foster a culture where it’s safe for people to report mistakes or suspicious activity without any fear of blame. To help you structure your programme, you might find our guide to staff cyber security training for NZ businesses useful.
By combining these technical and cultural elements, you start to build a robust and proactive defence that properly protects your business from the ever-present threat of cyber crime.
How to Build an Effective Incident Response Plan
When a cyber attack hits, those first few minutes and hours are everything. A solid, well-thought-out Incident Response (IR) plan is what turns that initial chaos into a structured, effective recovery. It's the difference between panic and process, helping to minimise both financial loss and reputational damage from cyber crime in NZ.
Think of it less as a dusty document and more as a practical playbook for your team to grab during a high-stress event. The goal is to get everyone out of a reactive mindset and into a state of prepared readiness. Following a clear set of steps ensures your response is fast, compliant, and coordinated, massively improving your odds of a successful recovery. When putting your plan together, using a good standard operating procedure template can make sure you cover all the critical bases.
Key Phases of Incident Response
A truly effective IR plan isn't just a single checklist; it's a lifecycle broken down into six distinct phases. Each stage has a clear purpose, guiding your team from the first sign of trouble all the way through to post-incident review. This structure is vital for making sure nothing gets missed when the pressure is on.
Preparation: This is all the work you do before an incident. It’s about getting your response team identified, defining who does what, and making sure all the necessary tools and communication channels are ready to go.
Identification: This phase kicks off the moment something unusual is spotted. The goal here is to quickly figure out if you're dealing with a genuine security incident, assess its scale, and get a handle on its potential impact on the business.
Containment: Once you've confirmed an incident, the first priority is to stop the bleeding. You need to contain the threat and prevent it from spreading further. This could mean isolating affected systems from the network or temporarily shutting down certain services.
Eradication: With the threat boxed in, the next step is to remove it from your environment completely. This is about getting to the root cause, whether that’s deleting malware or patching the vulnerability that the attackers exploited in the first place.
Recovery: Once the threat has been dealt with, it's time to safely bring your systems back to life. This phase is all about restoring affected systems and data from clean backups, making absolutely sure they're secure before they go back online to serve customers.
Lessons Learned: The incident might be over, but the work isn't. It's crucial to conduct a thorough review to analyse what happened, what went right with your response, and where the gaps were. These insights are gold for strengthening your security and updating your IR plan for next time.
Making Your Plan Actionable
A plan is only worth the paper it’s written on if it actually works in the real world. You need to test it. Regularly.
Running drills and tabletop exercises ensures everyone knows their role and that your procedures hold up under pressure. An IR plan should be a living document that grows and changes with your business and the ever-shifting threat landscape.
An Incident Response Plan is not just an IT document; it is a core component of business resilience. It ensures that when an incident occurs, your response is driven by clear process, not panic.
This structured approach to handling incidents ties directly into your broader operational resilience. For a deeper look at how this fits into your overall strategy, check out our guide to business continuity planning for resilient Kiwi SMEs.
Frequently Asked Questions About Cyber Crime in NZ
When you're dealing with a potential security incident, things can get stressful, fast. This section is here to answer some of the most common and urgent questions we hear from New Zealand businesses, offering clear, practical advice to help you prepare and respond.
What Are the First Steps After a Suspected Breach?
If you think you've been breached, the key is to act quickly but calmly. Your first move should be to contain the threat. This means isolating the affected computers or systems from the rest of your network to stop the problem from spreading any further. It's critical that you don't delete anything, as that could wipe out vital evidence needed for the investigation.
Once contained, your next step is to figure out what happened and how big the problem is. This is where your incident response plan comes into play. Start following the steps you've laid out and get in touch with CERT NZ for expert guidance on what to do next.
What Are the Hidden Costs of a Cyber Attack?
The upfront financial loss from a cyber attack is often just the tip of the iceberg. The real damage, the stuff that can hurt a business for years, is often hidden.
These long-term costs can be far more devastating and usually include a few key things:
Reputational Damage: Trust is hard to win and easy to lose. A breach can seriously damage your brand's reputation with customers, which directly impacts future sales.
Operational Downtime: It's simple maths. Every hour your systems are offline is an hour of lost productivity, lost sales, and lost revenue.
Legal and Regulatory Fines: If you don't handle a data breach correctly under the Privacy Act, you could be facing some hefty penalties.
Increased Insurance Premiums: After a security incident, it’s almost a guarantee that your cyber insurance costs will go up.
How Can I Tell If My Security Is Good Enough?
Checking your security isn't a one-and-done task; it's something you need to be doing all the time. A good place to start is with a proper risk assessment to pinpoint your most critical assets and identify your weakest points.
A strong indicator of adequate security is having a multi-layered defence. This means combining technical controls like Multi-Factor Authentication (MFA) with regular staff training and a tested incident response plan. If you are missing any of these key elements, your defences have critical gaps.
Beyond that, you should be regularly testing your backups to make sure they work, running phishing simulations to keep your team sharp, and staying up-to-date on the latest threats targeting businesses here in New Zealand.
When it comes to the rising tide of cyber crime, a proactive and resilient defence is your best strategy. Wisely provides expert managed IT and cybersecurity services designed to protect NZ businesses. We can help you build a robust security framework, from implementing essential technical controls to developing a comprehensive incident response plan. Secure your business and book a consultation at https://www.wiselyglobal.tech.
Comments